Tor hidden services allow various types of services (web server, telnet server, chat server, etc) to be operated within the Tor network. This allows both users and service operators to conceal their identities and locations. Just about anything that can be run on the clearnet can be run within the Tor darknet.
Hidden Services are called "hidden" because your website’s IP in ToR is hidden - they cannot see the IP of your server — they can’t track you. An onion service needs to advertise its existence in the Tor network before clients will be able to contact it. Therefore, the service randomly picks some relays, builds circuits to them, and asks them to act as introduction points by telling them its public key.
Setting up a hidden service on Tor is a simple process and depending on the level of detail, an operator can keep their service completely anonymous. Depending on your use case, you may or may not choose to anonymize your service at all. For anonymous operation, it is recommended to bind services being offered to localhost and make sure that they do not leak information such as an IP address or hostname in any situation (such as with error messages).
Setting up the hidden service
Prerequisite
- A virtual machine to host the hidden service with Ubuntu or Debian installed and root access
Download Tor
Edit the /etc/apt/sources.list file and based on your OS, make the relevant entries at the end of the file
Ubuntu Bionic Beaver (18.04 LTS)
Ubuntu Xenial Xerus (16.04 LTS)
Debian Jessie
Debian Stretch
Then add the gpg key used to sign the packages by running the following commands at your command prompt:
Now to install Tor, run the following commands
Configure torrc file
Edit the torrc file
nano /etc/tor/torrc
Find the section where it says "This section is just for location-hidden services". Uncomment the two lines below:
HiddenServiceDir is where you'll find the hostname and its private key. We will change this to /var/lib/tor/hideme/HiddenServicePort tell Tor on which port it should listen to and on which port it should forward the request. We will change it to 80 127.0.0.1:8000. Tor will listen to port 80 and forward to at port 8000.
Save the file and exit. Now restart the Tor service.
sudo systemctl restart tor
Install and Setup NGINX
First, install the NGINX server
apt install nginx -y
We will delete the default configuration file of NGINX
rm /etc/nginx/sites-enabled/default
Now we will create a configuration file for our hidden service
nano /etc/nginx/sites-available/hideme.conf
In the editor, enter the following lines:
Create a symbolic link of the configuration file to the sites-enabled directory
ln -s /etc/nginx/sites-available/hideme.conf /etc/nginx/sites-enabled/hideme.conf
Restart the NGINX server
service nginx restart
Now we will create an index file in html directory to be server over Tor hidden service
nano /var/www/html/index.html
Add the following lines in the editor window
Save the file and exit.
Get onion address
We will find the onion address of our service in the directory entered against HiddenServiceDir in the torrc file.
cd /var/lib/tor/hideme/
Run ls to ensure that there are both the hostname and private_key file. View the hostname by running
cat hostname
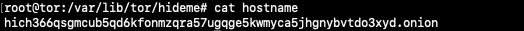
You will get a 56-character long onion address. Copy this address.
Test the configuration
Open the Tor browser and enter the hostname that we obtained in the previous step.
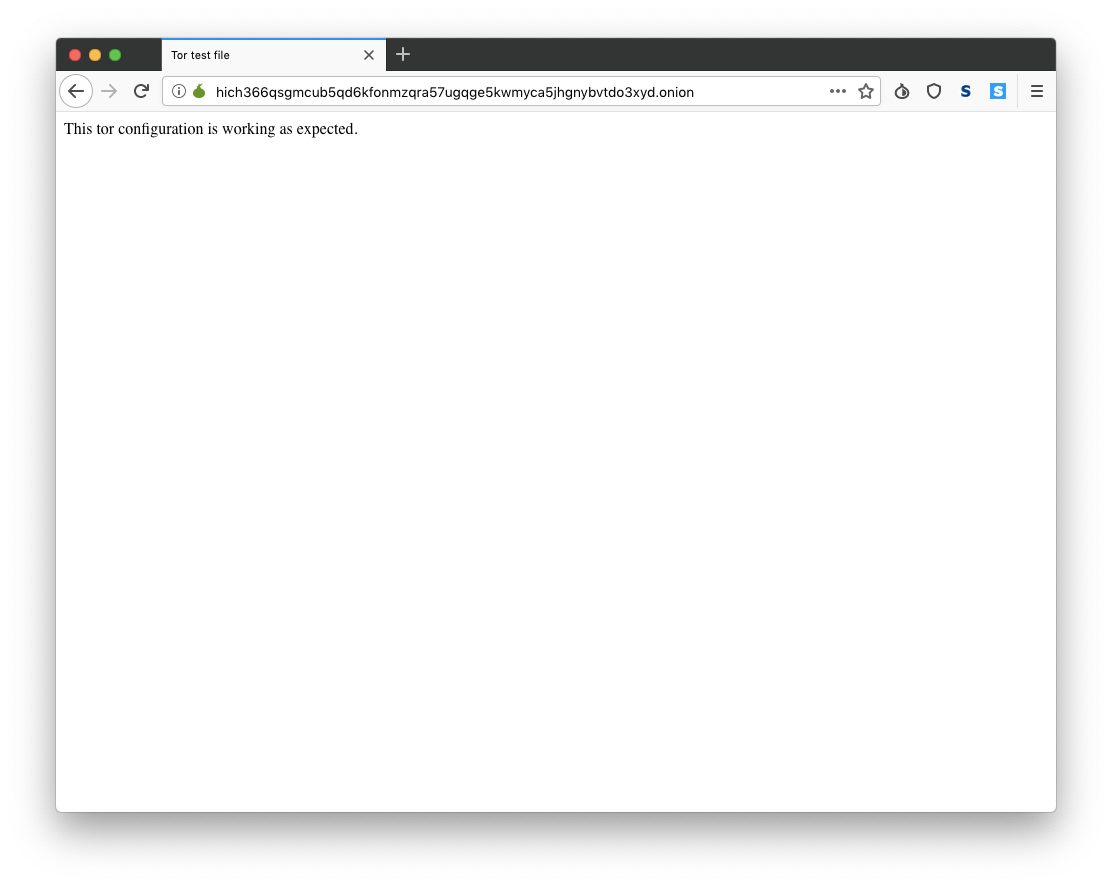
If you get a screen like this, you have successfully configured your Tor hidden service.
Onion address v3 vs v2
By default, in the latest version of Tor, you will get a v3 onion address that is 56 characters long. If you wish you use 16 characters long v2 address, edit the torrc file and replace the previous configuration with the lines below
Restart Tor by running systemctl restart tor
Find your new hostname
cat /var/lib/tor/hideme/hostname
Tor by no means is illegal. Many search engines and even Facebook provide service over Tor for countries with heavy censorship.
Facebook has its onion service at www.facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion and duckduckgo runs on duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion. You can also view this blog on blog.rishabhl5pg7fr6jniteopb76jc67x4pyzbljsbaopt7xcxszp7hqnyd.onion using TOR Browser.

